Math Cryptography Examples | Constructing hyperelliptic curves of genus 2 suitable for cryptography. Whenever we come across the term cryptography, the first thing and probably the only thing that comes to our mind is private communication through encrypti. Cryptography for algorithms and cryptography. It is a method of storing and transmitting data in a particular form so that. The math behind cryptography is immensely fascinating, i could spend all day studying it!
The book gathers the main mathematical topics related to public key cryptography and provides an excellent source of information for both students and researchers interested in the field. The book focuses on these key topics while developing the mathematical tools needed for the construction and security analysis of. Primes, modular arithmetic, and public key cryptography every cipher we have worked with up to this point has been what is. Cryptography has for long been an important issue in the realm of computers. Primes, modular arithmetic, and public key cryptography (april 15, 2004).

It involves storing secret information with a key that people must have in order to access the raw data. Cryptography lives at an intersection of math and computer science. And then you have the basic math background to learn about cryptography, which isn't just the math but also involves using the math in secure ways. It was mainly used for the security needed for passwords but now cryptography is very important due to the internet's flow. Constructing hyperelliptic curves of genus 2 suitable for cryptography. The book gathers the main mathematical topics related to public key cryptography and provides an excellent source of information for both students and researchers interested in the field. Cryptography, at its most basic, is the science of using codes and ciphers to protect messages. All that cryptography is, is mathematical functions. A collection of examples using solidity. Not right very well, that well comes. The first documented use of while the examples above are trivial, they do represent two of the functional pairs that are used with pkc. Cryptography — the science of secret writing — is an ancient art; Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of third parties called adversaries.
Primes, modular arithmetic, and public key cryptography (april 15, 2004). A collection of examples using solidity. Cryptography, at its most basic, is the science of using codes and ciphers to protect messages. This subreddit is intended for for example, elliptic curve cryptography defines the sum of two numbers as the third point on a line. Primes, modular arithmetic, and public key cryptography every cipher we have worked with up to this point has been what is.

Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of third parties called adversaries. Cryptography for algorithms and cryptography. Math is the basis for cryptography. It involves storing secret information with a key that people must have in order to. A collection of examples using solidity. .key cryptography (for example a course aimed at math majors) then i suggest covering chapters 3, 11 advised to skip chapters 2, 12 and 13, since these chapters are more mathematical in nature. An example would be any of the current encryption standards/methods like rsa. This subreddit is intended for for example, elliptic curve cryptography defines the sum of two numbers as the third point on a line. Constructing hyperelliptic curves of genus 2 suitable for cryptography. It is a method of storing and transmitting data in a particular form so that. Whenever we come across the term cryptography, the first thing and probably the only thing that comes to our mind is private communication through encrypti. It was mainly used for the security needed for passwords but now cryptography is very important due to the internet's flow. If we pick the modulus 5, then our solutions are required to be in the set {0, 1, 2, 3, 4}.
It is a method of storing and transmitting data in a particular form so that. Constructing hyperelliptic curves of genus 2 suitable for cryptography. Cryptography — the science of secret writing — is an ancient art; Math is the basis for cryptography. Cryptography lives at an intersection of math and computer science.
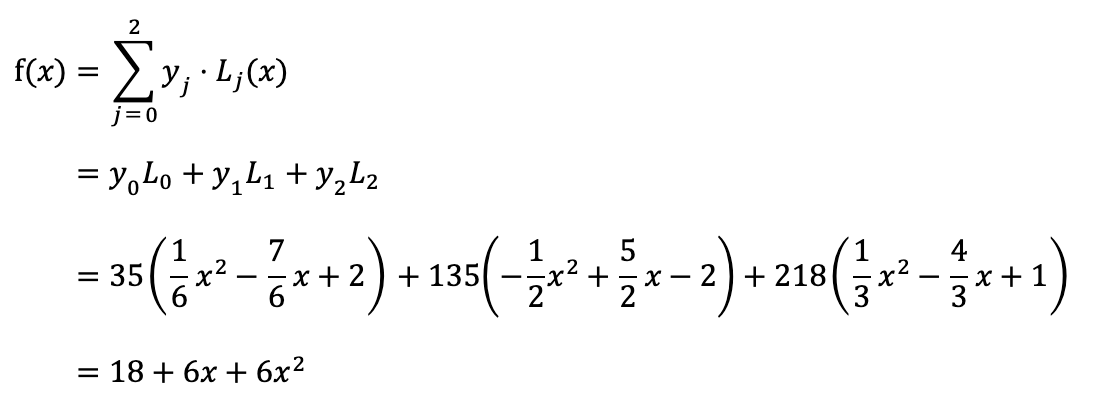
Primes, modular arithmetic, and public key cryptography (april 15, 2004). This subreddit is intended for for example, elliptic curve cryptography defines the sum of two numbers as the third point on a line. It is a method of storing and transmitting data in a particular form so that. Not right very well, that well comes. Math circle thursday january 22, 2015. Cryptography for algorithms and cryptography. It was mainly used for the security needed for passwords but now cryptography is very important due to the internet's flow. Cryptography is the science of using mathematics to hide data behind encryption. We have 2+1=3 and 2+2. The book focuses on these key topics while developing the mathematical tools needed for the construction and security analysis of. Shiftcryptosystem(alphabeticstrings()) shift cryptosystem on free sage 9.2 reference manual: Cryptography, or cryptology, is the practice and study of techniques for secure communication in the presence of third parties called adversaries. Constructing hyperelliptic curves of genus 2 suitable for cryptography.
Math circle thursday january 22, 2015 cryptography examples. The book gathers the main mathematical topics related to public key cryptography and provides an excellent source of information for both students and researchers interested in the field.
Math Cryptography Examples: An example would be any of the current encryption standards/methods like rsa.
Source: Math Cryptography Examples
EmoticonEmoticon